According to a WikiLeaks’ archive of over 400 GB of data leaked from the Hacking Team’s servers that were hacked a fortnight ago shocking details reveal email exchanges between different workers of the spyware manufacturer, the Uganda Police Force (UPF) and the “Office of the President.” In total, there are 166 emails that mentioned Uganda ranging on a couple of issues such as security prospects, economic development, but the last email thread predating the periods between April and July 2015 spills what the malware-manufacturer discussed with UPF. An algorithms arms of trade involving sale of spyware (spying software). This leak is in the public interest and I believe the damage to the protagonists is smaller. However, we’ll only realize the greater benefit if we focus on the bigger picture rather than being excited by the Juicy details. Hacking Team, according to the email leaks, deals in the vending of sophisticated malware and surveillance software to security outfits. They have dealt with several countries all over the planet from those that have oppressive regimes such as Bahrain, Morocco, Ethiopia and Sudan to surprisingly, the U.S and Russia, countries which one would expect to have in house or home grown hacking/surveillance tools. According to a former worker of Hacking Team, the scariest implications of these surveillance technologies are discerned and discussed in three things: evidence planters, kill switches and backdoors. He argues that presence of any one of them would imply that the systems are compromised beyond doubt. Here is a summary of what each of the elements means. In a sort of knee jerk reaction, the Hacking Team was quick to report of the imminent dangers of its crafted malware landing in the wrong hands; terrorists. Even if that was the case, the malware is not a weapon of threat because its inherent value lies in secrecy, which by extension of the hack is already exposed and therefore lacking in value and threat. And that is the same approach state agencies usually take when confronted with such dilemmas, they create quasi sensitive situations to diverge the attention of the media, even when the material facts say otherwise. In an exclusive video interview with CCTV on 19th April 2015, Jimmy Hagume, the Head of Cybercrime UPF articulated, on the record, that cases of looming terrorism activities on social media were minimal and if there existed any, they would be thwarted in no time. He added, “We are blessed and maybe fortunate that we have not had a trend where people have believed radicalization or ideology that is sweeping across other nations and other continents, and what I can say is that people mainly are using traditional methods, if they were told to communicate message, they would use a mobile phone, promise to send you mobile money or even walk to your home to use a friend to convince you to meet.” True, there is a modicum of threat in rough clay, using traditional methods to gain form and there are enough measures and tools, still, to mitigate them. For example wiretapping phone calls, screening text messages all that are enabled by the Interception of Communications Act, 2010 which was championed by the former Premier of Uganda. Late last year, the process of purchasing a sophisticated phone-tapping machine at a tune of UGX 205 billion was finalized. But here is what is shocking and calls for transparency, the surveillance software that Uganda is planning to buy or has already bought from Hacking Team is called RCS (Remote Control System) or creatively named Galileo, sometimes Da Vinci. According to a thread of back to back emails addressed to the Head of ICT UPF, Director Amos Ngabirano, the system is poised to have been launched in earnest by mid this month (July 2015). Notably, RCS targets computers and mobile devices of popular platforms which are Windows, Linux, Apple to steal and transmit data. What is debilitating is that the stolen data can be transferred without an active internet connection. In summary RCS’s capabilities include the ability to copy files from a computer’s hard disk, record skype calls, e-mails, instant messages, and passwords typed into a web browser. It can also turn on a device’s webcam and microphone to spy on the target. For whistleblowers who hide behind the secure encryption by Tor and other apps, RCS could potentially unveil the mask. So if we go by the parameters that terrorism on social media and the internet at large is on a lower scale in Uganda, then what would be the reason for investment of colossal amounts of tax payers’ money in such surveillance systems? Security: Of course, this comes first. With advancement in technological innovation comes increase in technological threats. Besides, defence and military budgets are classified, so definitely we’d never know what figures are justified for expense in acquisition of defence tools and assortment of weapons. Surveillance is not new, it has existed from time immemorial. From the look of things nowadays, the arena is entirely on the cyberspace and a lot of gymnastics are being showcased. Another classic case was a research conducted by a German researcher about NSA’s nifty spying tools in 2007, their capability to sniff into a wi-fi connection 13 Km away. The research that was presented at the end of 2013, 6 years later, highlighted a related case where spying-gone-bad had Wikileaks founder Julian Assange receive text messages from a Ugandan telecom number. As suspected, the GCHQ could simply have forgotten to reformat the device from an earlier Ugandan operation. So here we’re, it’s not only countries spying on their citizens but also heckling with each other in the cyber-espionage space. Well, the issues of the state are issues of the state. There is no ambiguity in that, all animals are equal but in some distinct cases some animals are more equal than others.
The case of Justin Bieber, relax! Let’s build context here
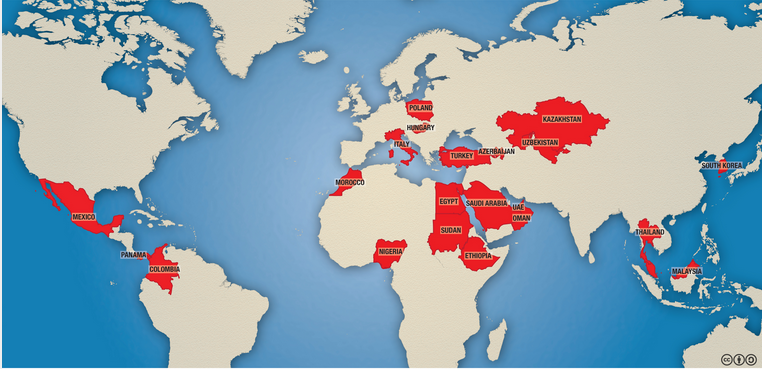
The year is 2014, the first month of the year and Americans are going irate, their anger is stemming from pop star, Justin Bieber’s unbecoming characters – driving under the influence of alcohol and apparently desisting arrest – they say, that sets a misleading example to their children and youth from who he enjoys a cult like following. The responsible citizens are attuned to having their moral compasses facing north, straight upwards. They want him deported to Canada and his green card revoked too. They took the fight online, not on social media but on the United States’ White House official website. Within 30 days, they had hit 100,000 petitions from real people, real Americans. It took up to 3 months, the number of petitions standing at 273,968, such an overwhelming number, that the White House communications department made a pronouncement on the petition, that they couldn’t deport the pop star because of several technical issues. That was a side step against the people’s will, their voice and democracy, if I must drag that in. The point is governments world over are not as worried of the hashtags that we continue to prop up every other day on social media the way we may want to think. They’re just paranoid about the day to day information we share. Behind text messages, phone calls, bank transactions to mention but a few. Be the dragons behind the enormous data we share, if sniffed and methodically analyzed, shocking patterns may be found; from the impending terror attacks in plan, to the political sentiment among the public, income spending habits, the list is just endless. The list has a fancy title though, Big Data! Whoah! I’d like to think that this big data is comprised of exabytes of useless cat videos, gifs and a bunch load of emotionally charged narcissistic Facebook posts. Of course we’re the new generation, some have touted us as the mobile first generation, we love technology, when we start tweeting away, we’re a borg, we’re mavericks. People have an unassailable hope in technology, they have this hope that it’s the crystal ball they have been waiting to use to score their ways out. In today’s world, location and time constraints are close to negligible, everything is instant. Whereas you’re more excited about advancements in technology, planning to livestream a regime change caused and effected through a #hashtag with a matte cased rectangular device in our hands, companies and security agencies then must be plussing 1000 to the heavens for more better opportunities to carve adverts that follow you home or even effecting 24-hour surveillance on you through that smartphone that is alienating you from people. Let’s not discredit technology, the World Wide Web or even social media at large. For example it has been used to take down suppressing governments, the Arab Spring uprising in 2011 bears witness. Boy, change has happened because of technology. A lot of it. And that’s why governments and security agencies in particular are interested in cyber-whatever; warfare, security, surveillance, name it. They are not taking any chances. The laws to curb purported abuse of the cyber space are in place although some, the tinging ones like PIPA and SOPA are being remodeled and repurposed. The cyber security industry is worth $75 billion in 2015, and analysts forecast that it will be about $170 billion in 2020. Companies and government agencies are spending a lot of resources to insulate themselves against cyber threats which are raising rapidly. Some are stalking us. Obsessively, and it’s worrying. An infographic by Citizen Lab in 2014 showing the suspected clientele to Hacking Team, now that the details are in the public domain, it turns out that Uganda is not yet included on the official list as shown by the tweet below.
— Spartakussug (@spartakussug) July 21, 2015 Perhaps we’re to blame, we give up so much information about ourselves online. Those of us addicted to such wistful ways are like the proverbial canaries in the coal mine, the first to drop of oxygen deprivation. Information is nothing if no one notices it, pays attention to it. When you scroll down the stream of Facebook posts or Twitter updates, Instagram photos, you may pay attention to only a dozen posts and it’s most likely other people will behave in the same way, a lot of information effervesces in the stream just like that. But secrets are different, their worth is ostensibly high especially when their nature is nefarious. Trading such is some sort of currency, a new currency independent of cold hard cash notes but rather one that is potent and consequential if ever exposed on to the public realm. Now you know. Image: Edited | illustration by Tim McDonagh for Matter