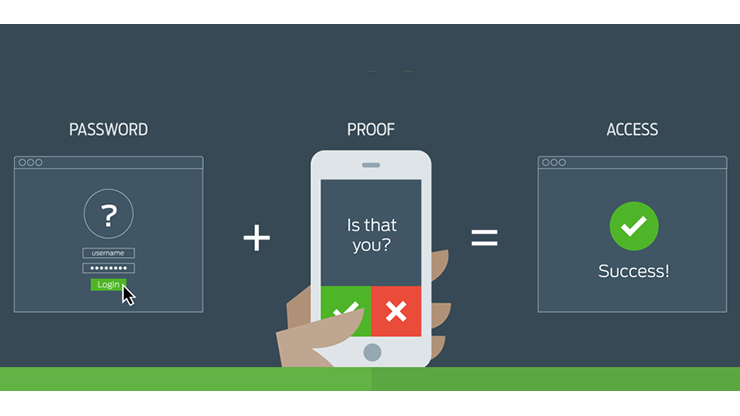
These authentication factors can be a piece of information like a password, keycard, or fingerprint. On the other hand, 2-Factor Authentication (2FA) is a type of Multi-Factor Authentication that employs two authentication factors that are distinct. With 2FA it has to be factors under two different categories of authentication. Like something you possess or something you know. A good example is when you try to log into an online service via your computer using a username and password, where you are then sent a push notification on your phone to confirm the login. Finally, 2-Step Verification (2SV) is also a type of Multi-Factor Authentication that demands two authentication factors via two sequential verification steps. For instance, Google uses this 2SV where you have to input a username, password, and an additional code to be able to log in. The key point here is that both 2FA and 2SV are types of Multi-Factor Authentication that can extend to 3FA or 3SV and so on. The main difference between all these boils down to the method of authentication that is applied. Essentially if a login process has two steps it will be a 2SV. But if those two steps use varying factors it becomes a 2FA. Also Read:
What is Universal 2nd Factor(u2f )key?How to sign into a Microsoft Account without a Password
Main Types of Authentication Factors Used by MFA, 2FA and 2SV
There exist several ways and solutions to authenticate access to a system and confirm the identity of a user. That is over and above the usual username and password. Each of these secondary methods of verification will fall into one of four factors or categories. They all relate to either the location of the user, their knowledge, their other devices, or their biometrics.
1. What The User Knows
Using a piece of personal information that is known by the user only is the most common way to authenticate and verify system access. This is what we are referring to as knowledge unique to the user. This can be a piece of information or characters they need to submit. The most used one is where you need to input a personal identification number (PIN) on top of a password and a username. When the PIN and password are used sequentially it is 2SV. Other times you will be prompted to enter information such as your first school, and your mother’s maiden name. Or where you were born, etc. This is usually not too secure as this is information that one can find with relative ease through social media. Also Read:
Titan security key is Google’s latest way of securing user dataWhat is Two-Factor Authentication and why should you use it
2. Something The User Possesses
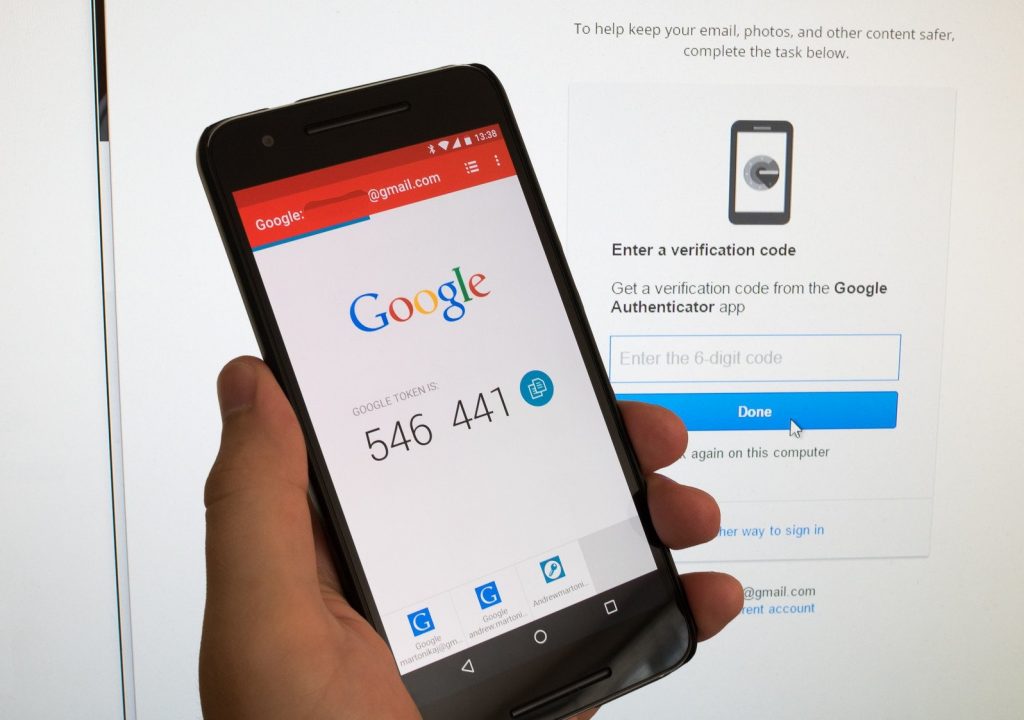
Using something that a user has with them is another popular factor for verifying system access. This is something like a smartphone, key card, or hardware token. With smartphones, this includes 2FA applications that you can download to your phone. These are the likes of LastPass Authenticator, Google Authenticator, and Microsoft Authenticator. They can also be installed on your computer. In principle, the possession factor can also be considered as a knowledge factor above. This is because your device or application will require you to know an additional password. Important to note is that hardware tokens like Token2 and YubiKey also function similarly to 2FA apps. However, the user inserts a key linked to their identity that displays a new code every time they need to log in. Those SMS codes sent to your phone to verify access fall under this category. However, they are not recommended in robust MFA solutions because they come in plain unencrypted text that can be easily spoofed
3. Biometrics of The User
Various kinds of biometrics like voice recognition, facial recognition, fingerprints, and eye scans are now widely used to ascertain the identity of a user. These are used mainly at on-premise locations as well as in many personal electronics like phones. There is hardly a premium phone on the market without both fingerprint recognition and facial recognition.
4. Location of The User
Many blue chip companies employ a system where you can log in to their corporate network with just a username and password if you are on-site. However, when the installed hardware token detects that you are offsite, you will be prompted with a 2FA to log in. This is a kind of scenario where the location of the user will determine what factor will be used to authenticate their identity. Also Read:
How to Enable Two-Factor Authentication on Your Social Media AccountsThe Updated Guide to Online Privacy and Security
Choosing the Appropriate Authentication Method
None of the four methods above is superior to the others. The best solution will be dependent on your specific application. Generally, most organizations will tend to look for a balance between budget, security, and productivity. Imagine a super secure 7-step or 7-factor system that means employees spend considerable amounts of company time logging in every day. Yes, it is very safe, perhaps too safe, but at what cost? Again, think of a Multi-Factor Authentication system that will cost your company double the available budget. This is why we insist that choosing the appropriate method is a delicate balance of what costs you are willing to incur. Also, what levels of security are satisfactory to you? How efficient the system will be?
MFA vs 2FA vs 2SV: How They Compare
When it comes to choosing between 2SV and 2FA, technically 2FA is considered to be more secure than 2SV. This is because 2FA works with two different factors compared to 2SV which requires two steps of the same factor. 2FA will combine knowledge and possession authentications while 2SV will combine two knowledge authentications. Most of the time compliance requirements will require organizations to implement 2FA and not 2SV. On the flip side, 2SV is more user-friendly and faster as it may require two sets of information already in the knowledge of a user. Outside of compliance regulations, most organizations will resort to 2SV for productivity purposes. When it now comes to safeguarding valuable systems that hold critical information, MFA will be a prime candidate for implementation. Consider a situation where a user is required to input a password, and a pin and then scan a fingerprint to access data. This is a typical case of three steps of verification with two factors. We hope you now clearly understand the key differences between MFA, 2FA, and 2SV types of authentication as well as know how to choose the appropriate one for your application. For any follow-up queries, do not hesitate to reach us through the comments section below. Also Read:
Instagram to upgrade Two-Factor Authentication from Your Phone NumberLock down your Google and Facebook account with Two-Factor Authentication (2FA)